The blackmail algorithm
On 20th July 2015, Ashley Madison confirmed that hackers had breached its dating site for cheating spouses. Soon after, the first reports emerged of blackmail threats against the site's subscribers. But it's not just adulterers who should worry about the risk of being exposed…
20th July 2015 (Taken from: #20)
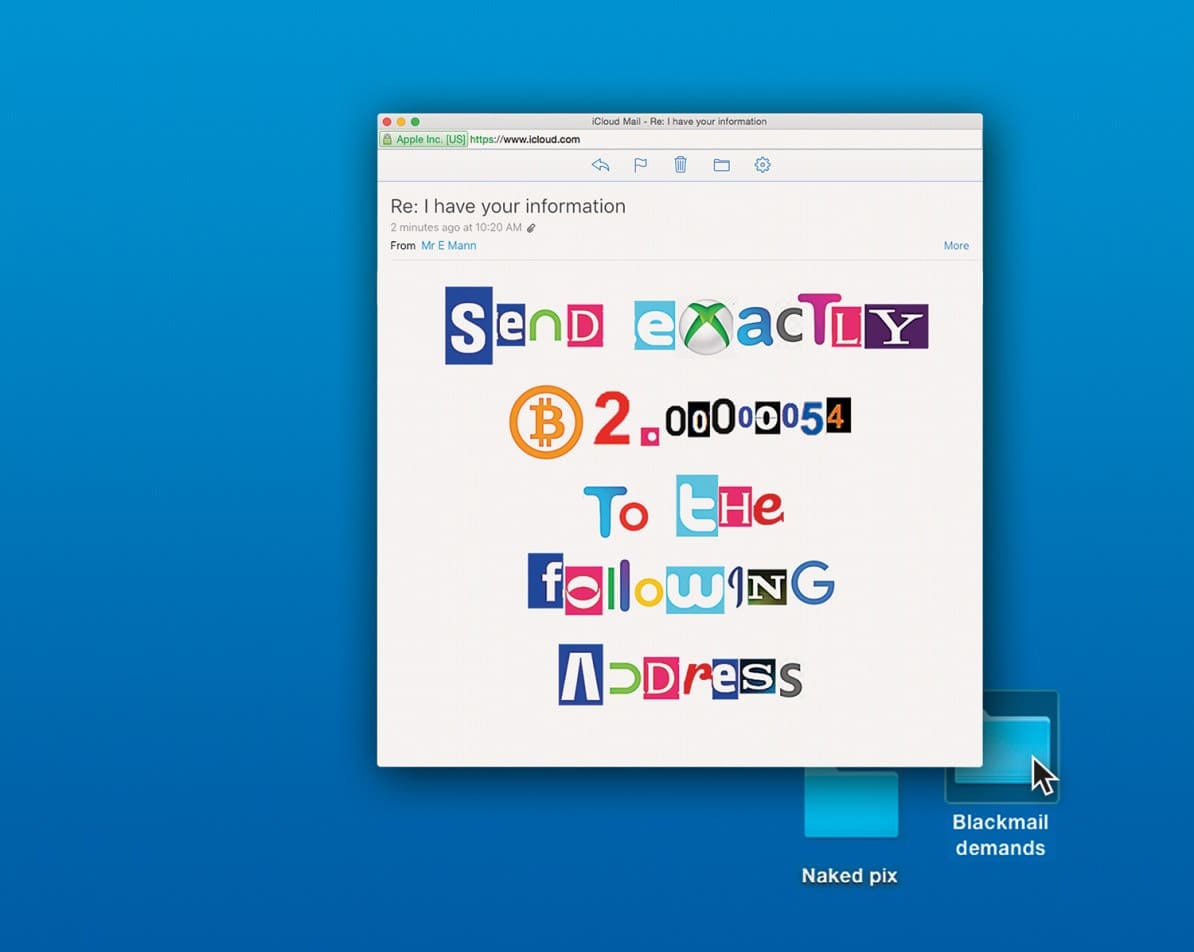
For all the hyperbole of online marketing, it’s rare that you receive an email that could genuinely change your life. The message that arrived in an unknown number of inboxes last August promised to do just that. “Unfortunately your data was leaked in the recent hacking of Ashley Madison and I now have your information,” it read. “If you would like to prevent me from finding and sharing this information with your significant other, send exactly 2.00000054 bitcoins [approximate value $650] to the following address…”
The hard sell continued: “Consider how expensive a divorce lawyer is. If you are no longer in a committed relationship then think about how this will affect your social standing amongst family and friends.”
The compromising information in question had been stolen from Ashley Madison, a dating site for married people (their tagline: “Life is short, have an affair”). The story sat in the sweet spot between serious consumer safety news and salacious tabloid fodder and consequently gained widespread coverage over the summer.
A hacker collective calling themselves the Impact Team took credit for the initial attack on Ashley Madison’s databases in July, and for several days boasted about the vast quantity of user data that it had managed to purloin from the site: names, email and home addresses, credit card information, search histories and even, it claimed, sexual fantasies.
The Impact Team claimed moral motives for their attack, posting an online manifesto which focused on Ashley Madison’s “Full Delete” service – whereby users could pay $19 to have their profile comprehensively wiped. The manifesto claimed that the service had brought in $1.7 million in revenue in 2014 and that it was fraudulent as, they claimed, user data was retained. Later the group switched their ethical ire onto the users of the site, in a release that accused them of “fraud, deceit and stupidity” for seeking to cheat on their spouses and encouraged them to “learn your lesson and make amends”.
What if the threat to leak our internet history, our credit score or our location on a certain day were enough to make us pay to silence a blackmailer?”
Having stated their motivations, the hackers laid out their ultimatum: the data haul would hit the public domain unless Ashley Madison was immediately shut down. The site remained up and, after drip-feeding user information onto the web over the course of a fortnight, the hackers opened the floodgates with a release of 25 gigabytes of Ashley Madison data.
Initially this cache was made available only to those who could access the so-called “dark web” using the anonymous browsing tool Tor, but it was soon copied out onto the wider internet using forums such as 4Chan, and anonymous text-posting services like Pastebin. And then, a short while later, the individual blackmail threats began.
It’s impossible to gauge the scale of the blackmail accurately, since many of those who paid out rather than risking exposure would have stayed quiet about the deal. But one thing has become clear from the initial investigations: in the current ecosystem of digital theft, the blackmailers are often not the same people as the hackers. The extorters in the Ashley Madison case appear to be mainly opportunistic criminals who have sifted through the email addresses that were released and cross-referenced them with social media to find the killer details (the names of partners and children etc) that will give the blackmail notes their sting.
“There’s a whole gamut of bored teenagers out there who just want to break into things, and then there are professional criminals who are intent on profit,” says Joseph O’Halloran, editor of Infosecurity magazine. “So if the teenagers release hacked data, the criminals can use it for malevolent purposes and to make money.”
That’s not to say that the hackers aren’t sometimes motivated by profit too. “You might have a group of hacktivists who break into an oil company website because it’s got a dodgy environmental record,” says O’Halloran. “They deface the website to embarrass the company. But then one of them realises that the data they got hold of has value, and goes rogue – decides to sell it to another group or on the dark web open market. That’s how it works these days.”
Digital Achilles’ heels
It’s difficult to summon much sympathy for people who signed up for Ashley Madison in order to betray their better halves – but it’s not just subscribers to infidelity sites who are open to online blackmail. In an age in which we’re storing ever-greater amounts of information online and trusting an ever-growing number of potentially vulnerable organisations to keep that data safe, the opportunities for criminals to find and exploit our weak spots are growing exponentially.
Photo: Lee Jin-man/AP/Press Association Images
Public embarrassment over sexual misdeeds was the biggest fear for those caught in the Ashley Madison hack. But what if rather than cheating on a spouse, an individual was using the internet to seek relations with someone of the same sex, but had yet to come out publicly as gay? Or if (like multiple female celebrities in 2014) they had stored in the cloud intimate pictures designed to be shared with a select few, rather than anyone with a web browser? What if the threat to leak our internet history, our credit score or our location on a certain day were enough to make us pay to silence a blackmailer?
Evidence of certain political or social views could also be a point of vulnerability. When in November 2015 the famed hacktivist collective Anonymous released the names – and other details – of leading members of the Ku Klux Klan, nobody was protesting on grounds of civil liberties (racists in pillowcases rank much lower than cheating spouses in the international sympathy index). But people are very subjective when it comes to politics. What if your potential new employer objects to your membership of a left wing party? What if the person reviewing your visa application could be shown how many anti-war demos you’ve been on? And then there’s medical data. If you’re a recovering alcoholic, HIV positive, or have a mental health condition that’s being treated with medication, all of this information is stored somewhere, ready to be stolen.
“The trend towards more data being digitised brings benefits – with health data, for example, you can increasingly access it online,” says O’Halloran. “But it may be things that you don’t want your employer or family to know – and certainly don’t want your insurer to know.”
The data magicians
Ashley Madison offered some low-hanging fruit for blackmailers: here was a group of people who clearly had something to hide. But the next wave of blackmailers could use algorithms to comb multiple sources of breached data and identify targets who are open to extortion, weaving together data sources that expose their weak spots. “Think about how magicians work,” says O’Halloran. “They know that we transmit information in our expressions and the way we speak, and it’s measurable – we’re telling them what’s really on our mind. A skillful magician knows how to build a picture out of this jigsaw of information. It’s exactly the same with digital data.”
And this data dragnet can now cover the “internet of things” alongside our desktop computer browsers. Fitbits and Apple Watches record our heart rates and a host of emerging tech startups are finding new ways to measure our behaviour through everything from our wifi-enabled fridges to our cars. Our awareness of which devices connect to the web is lagging behind the technology. “People don’t understand how many devices they have that are connected, and not necessarily secure,” says O’Halloran. “Things like video cameras, drones, the central heating you control with an app, or remote home security cameras. Flat screen TVs… often transmit data back to the vendor. People aren’t aware of this. This Christmas, millions of people are going to be unwrapping presents that are connected, so this is going to be a greater risk in 2016.”
Your most important device when it comes to posting data online, however, is your phone. “Smartphones will remain the king of devices because we take them with us everywhere,” says Geoff White of Channel 4 News, a specialist in data security. “Phone apps are always running unless you make the effort to switch them off and there are some that are still running in the background even after you switch them off, so the data trail continues.”
He points out that you may be sharing data from your phone with far more people than you think. “Let’s say you use a social network and you share pictures with it… If every time you want to look at your photographs on your network your phone has to call out the US, get the picture and take it all the way back, that’s a lot of work for your phone to do. It slows things down. So a lot of social networks say they’ll store pictures nearer to you, in Amsterdam, London or Berlin… [meaning] our content is stored by third parties and we don’t usually know who or where they are.” This means our information can be hacked from many more places than we think, which matters because, as White puts it, “data is your value, data is money, data is like a stack of banknotes.”
And hackers are getting better at accessing the vast security-protected data dumps online. One favourite tactic, known as an “SQL injection attack”, focuses on software applications running on the target site, inserting malicious code into entry fields (in an online form, for instance) that can then access the site’s backend databases and pry out the contents. The hackers are always improving and refining their methods, too. “The bad guys are more innovative,” says O’Halloran. Right now, groups around the world are “developing algorithms and state-of-the-art data mining techniques. They may use these themselves, but they can also sell the code to others.”
In the second half of 2015, a series of telecoms companies were hit by significant data breaches. More information is being added to the swirling mass of data on the dark web every day. And with each new hack, the opportunity grows for blackmailers to send those heart-sinking demands for money. “Unfortunately your data was leaked, and I now have your information…”
Slow Journalism in your inbox, plus infographics, offers and more: sign up for the free DG newsletter. Sign me up
Thanks for signing up.








